Our security awareness training partner, KnowBe4, recently released the Top 10 Global Phishing Email Subject Lines for Q2 2017 report. The list below shows the subject lines of the phishing emails that are top clicked of all global phishing emails:
Security Alert – 21%
Revised Vacation & Sick Time Policy – 14%
UPS Label Delivery 1ZBE312TNY00015011 – 10%
BREAKING: United Airlines Passenger Dies from Brain Hemorrhage – VIDEO – 10%
A Delivery Attempt was made – 10%
All Employees: Update your Healthcare Info – 9%
Change of Password Required Immediately – 8%
Password Check Required Immediately – 7%
Unusual sign-in activity – 6%
Urgent Action Required – 6%
*Capitalization is as it was in the phishing test subject line
“The subject lines we are reporting here actually made it through all the corporate filters and into the inbox of an employee. That’s astounding. We are in a security arms race, and a multi-layered defense is critical because each layer has different points of effectiveness and ineffectiveness,” said Perry Carpenter, chief evangelist and strategy officer at KnowBe4.
“If crafted correctly, the right type of message can sail through all of the defenses because it is finding the least effective point of each and playing into the human psyche of wanting to receive something you didn’t know about or needing to intervene before something is taken away. Ultimately this means that a company’s ‘human firewall’ is an essential element of organizational security because people truly are the last line of defense.”
Employees are your last line of defense. Learn more about the security awareness training offered and managed through Cybriant: https://www.cybriant.com/home/services/strategic/training/
 Businesses have to also be aware that social media messages to their users are potential landmines to their corporate networks. KnowBe4 evaluated the Top 10 Global Social Networking Subject Lines and found that four of the top 10 spots equaling a full 44 percent were related to LinkedIn messages, which users often have tied to their work email addresses.
Businesses have to also be aware that social media messages to their users are potential landmines to their corporate networks. KnowBe4 evaluated the Top 10 Global Social Networking Subject Lines and found that four of the top 10 spots equaling a full 44 percent were related to LinkedIn messages, which users often have tied to their work email addresses.
As part of its ongoing research efforts, In October 2016 KnowBe4 evaluated more than 10,000 email servers and found that 82 percent of them were misconfigured, allowing spoofed emails to successfully bypass endpoint security systems and enter an organization’s network. Aggregating information on the most clicked phishing test subject lines and sharing that data with clients is another way that KnowBe4 is helping protect against social engineering tactics that continue to plague businesses around the globe, resulting in growing ransomware, CEO fraud and other phishing-initiated attacks.
Are you training your employees to become a “human firewall?” Take a look at the free tools that you can use to test your users and their network: https://www.cybriant.com/home/services/strategic/training/
Businesses that are not already working with KnowBe4 to effectively train their workforce into a “human firewall” can utilize a number of free tools at www.knowbe4.com to test their users and their network.
What is Firewall Logging and Why is it Important?
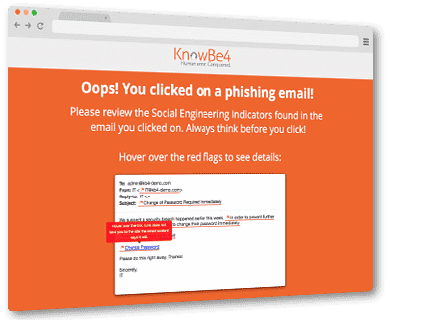





 Back in the early days of the Internet, phishing emails were full of typos and laden with obvious clues—appeals from faraway princess or rich relatives you never knew you had. These were very easy to spot. But cybercriminals have upped their game since then. For example, some cybercriminals go to great lengths to match the branding, color schemes, and logos associated with the companies they are trying to impersonate.
Back in the early days of the Internet, phishing emails were full of typos and laden with obvious clues—appeals from faraway princess or rich relatives you never knew you had. These were very easy to spot. But cybercriminals have upped their game since then. For example, some cybercriminals go to great lengths to match the branding, color schemes, and logos associated with the companies they are trying to impersonate.




