5 Reasons You Need a Mobile Security Risk Assessment

Here are 5 reasons to consider a mobile security risk assessment. Consider today’s most specific and hazardous security threat – our smartphones. These multi-purpose and ever-present devices should be included in your strategic cybersecurity plan including assessments and threat detection.
What Is A Penetration Test and Why Do You Need One?
Organizations that are focused on their security may consider several security assessments. But what is a penetration test and why do you need one?
How a Cyber Risk Assessment can Prevent Data Breaches

At Cybriant, we recommend every new client begin with a cyber risk assessment so your organization will have a full assessment of your current state of security, any gap analysis, and recommendations. Many compliance regulations stipulate the need for an annual risk assessment. Here are three ways a cyber risk assessment can help prevent data breaches.
7 Reasons You Need a Penetration Test in 2019

Penetration tests are an important piece of the cybersecurity puzzle. We like to begin with the end in mind and understand your goals before we recommend any assessments, gap analyses, or pen tests.
6 Considerations for Your Next Security Assessment Vendor

Information security assessments are a necessity in today’s cyber insecure world. Be sure to consider these 6 things when you select a security assessment vendor.
5 Key Reasons You Need a Cyber Security Assessment

You probably need a cyber security assessment, especially if you are wondering whether you need one. Here are the top 5 reasons you should get started…
People, Process, Technology in Cybersecurity or: How I Learned to Stop Worrying and Love the Process!

People, Process, and Technology is the cornerstone of ITIL, but can it also be used to ensure a proper cybersecurity foundation? The answer may surprise you!
Why You Must Perform A Security Assessment

Recently, we discussed why it is important to have a SIEM (Security Information and Event Management) system, and why it is crucial for skilled Administrators to actively use and monitor it. For a quick refresher, here is the article in Wired that sums up the presentation by Rob Joyce, Chief of NSA’s Tailored Access Operations, that inspired this series.This week’s post will cover why it’s important for your organization to perform a Security Assessment to analyze your organization’s operational risks.
Types of Network Security Threats and How to Combat Them

If you’re interested in the types of network security threats and how to combat them, you’re in the right spot. We’ll discuss a tried and true method to create a solid foundation for your network security.
NIST Cybersecurity Framework
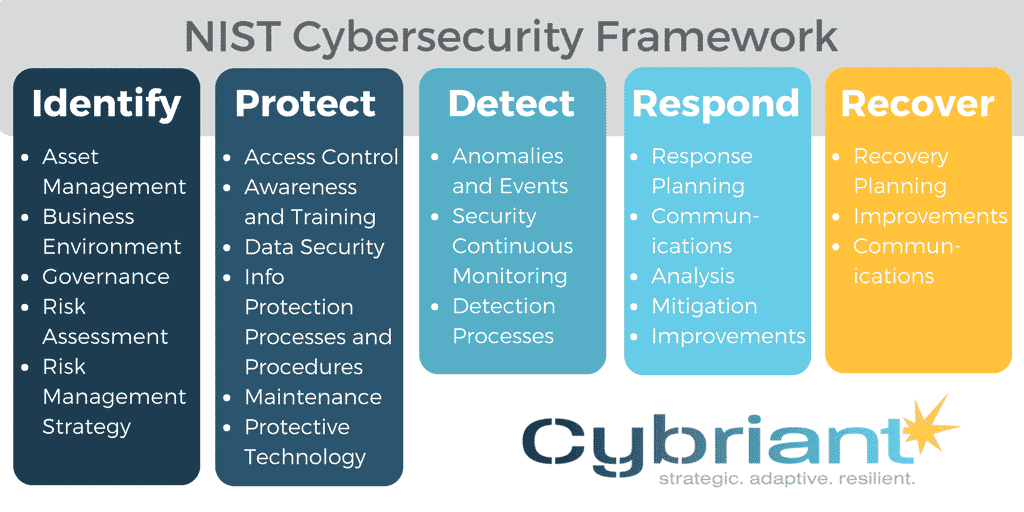
Organizations of all sizes need a solid security framework based on standards and best practices – a foundation to help you manage your cybersecurity-related risk. These standards should address interoperability, usability, and privacy based on the needs of your business.

