Your cyber security strategy should be as important as your legal, regulatory, financial, or operational strategy. Here are 10 steps to help define and communicate your strategy.
What Is Your Cyber Security Strategy?
Your cyber security strategy should help you move from a reactive to a proactive approach to cybersecurity. This strategy should include a security foundation that will help you form your plan of action that will result in the prevention of the theft of organizational and employee data.
In a recent report we learned that:
- Just 1 in 10 organizations say their current security solutions fully meet their needs.
- Nearly 9 out of 10 companies (87%) don’t have sufficient budget to implement effective cybersecurity systems.
In another article, “15 Shocking Stats about Endpoint Security Solutions,” we learned that:
- By 2021, cybercriminals will cost the world $11.4m each minute, fueled by greater ease of entry into cybercrime and more opportunities to leverage global events like COVID-19 in successful threat campaigns
- 20% of IT managers who were the victim of one or more cyberattacks last year can’t pinpoint how the attackers gained entry, and 17 percent don’t know how long the threat was in the environment before it was detected. Source
- Organizations are spending 85% of the time investigating non-issues, equivalent to around 41 days each year. Source
To begin the process of upgrading your cyber security strategy, it’s vital, to begin with, a security risk assessment. A Cyber Risk Assessment is a required step when determining the needs or success of your security program. When you outsource Cybriant for your assessments, our team of risk experts will follow NIST guidelines to perform interviews, documentation analysis, and walkthrough of physical areas to determine the state of the security program of the client.
How Do You Create a Cybersecurity Strategy?
It’s as simple as people, processes, and technology. Your organization should begin the strategic process by implementing a security foundation. Your foundation will make all decisions on people, processes, and technology much more streamlined. At Cybriant, we have built our services on the NIST cyber security foundation. Our services are aligned with the five functions of NIST – Identify, Protect, Detect, Respond, and Recover.
With a security risk assessment, you’ll have a better understanding of where your organization currently stands. An assessment will help you gain a better knowledge of your threat landscape, which will help you learn how to protect your organization.
Now that you have a foundation in place and an understanding of where you currently stand, what needs to be improved? What sort of budget do you have in place for security? What do you need to protect? Outsourcing the management of your cybersecurity will not only reduce your overall budget, but it will also give you:
#1. More In-Depth Services – Managed services are much more than threat detection and prevention, or just checking the boxes on compliance requirements. Depending on your needs, managed services can include email encryption, SIEM (security information and event management), IAM (identity and access management), endpoint protection, firewall protection, IDS/IPS, DLP (data loss prevention), and DRaaS (disaster recovery as a service).
#2. Operational Expense Budget – rather than taking a cut out of a large budget from capital expenses, managed services are charged every month.
#3. A High Level of Security Expertise – The only job of MSSPs is to keep you secure. There is no need for you to worry about finding cybersecurity talent, training, and maintaining them, your MSSP has a dedicated team of very highly-trained security analysts working for you full-time.
#4. Simplified Security – rather than maintaining a security portfolio of tens or hundreds of vendors, MSSPs stay updated on the latest in security technology so you don’t have to.
#5. Remediation – Not all MSSPs offer this service. But, Cybriant remediation is included in all managed services. Most MSSPs will alert you when something is wrong, but what if you don’t have the expertise to fix it? That’s where our team of security analysts walks you through the remediation process.
10 Steps to Upgrade Your Cyber Security Strategy
Your cyber security strategy should be communicated from the board room to the mail room. Defining and communicating your security strategy is central to the success of your organization’s security strategy.
Here are the 10 Steps to Cyber Security Strategy: #1. Network Security
You need tools in place to protect your networks from attack. These tools should defend the network perimeter, and filter out unauthorized access, and malicious content. It’s vital to monitor and test security controls as well. At Cybriant, this is our specialty. We offer 24/7 security monitoring services that will monitor your SIEM in our Managed SIEM service or your endpoints in our Managed Detection and Response service.
#2. User Education and Awareness
Your employees need to be aware of any user security policies covering acceptable and secure use of your systems. Be sure to maintain awareness of cyber risks. We recently discussed how employees are your #1 resource to keep your organization safe from cyber attacks:
By engaging your employees in understanding the importance of being aware of potential cyber threats, you are already ahead of the game. Reddit user mustaffaofberne had an interesting concept that helped take their “users who fall for phishing attempts” count down to zero.
After years of training, reminders, examples, and such that users have ignored, the IT department stumbled on a trick that seems to work. About 9 months ago a user submitted a ticket questioning a suspicious email, and IT replied by telling them “good job, you get a star!”.
An email was sent out to the entire company letting everyone know about the phishing attempt and that the user had been awarded a star (the emoji of a star, nothing else).
Since then, users have been reporting every phishing attempt, bragging about how many stars they’ve gotten, and debating about how stars should be able to be traded for pay raises or at least Schrute Bucks. It is just an emoji in an email, but everyone tries to get them.
It’s a great idea to get your employees involved and rewarded when they discover phishing attempts. Here are additional ways to keep your organization safe from cyber attacks by using corporate policies and best practices.
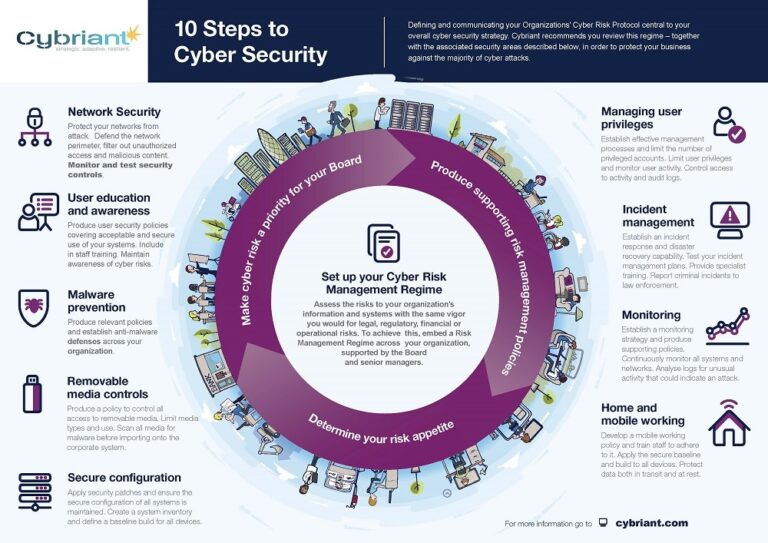
#3. Malware prevention
91% of cyberattacks start with a phish, and the top reasons people are duped by phishing emails are curiosity (13.7%), fear (13.4%), and urgency (13.2%), followed by reward/recognition, social, entertainment, and opportunity. Source Protecting your organization’s endpoints – including any employee-owned devices and employee-owned devices that can connect to your network – is an important piece of your cyber security strategy. An endpoint security solution like Managed Detection and Response will help establish anti-malware defenses across your organization.
#4. Removable media controls
The damage one single USB drive can do is alarming. It’s been proven that many people will pick up a USB drive that appears lost and will use it without hesitation. Plus, USB drives are guaranteed to be left behind or lost.
It’s important to get a better understanding of removable media that is being used in your organization. Produce a policy to control all access to removable media, this policy should limit media types and use. A service might be necessary to scan all media for malware before importing it onto the corporate system. A Firewall-as-a-Service with a next-gen firewall could help detect risks at the human level.
#5. Secure configuration
Remember the Equifax breach?
Equifax, one of the three major consumer credit reporting agencies, said that hackers had gained access to company data that potentially compromised sensitive information for 143 million American consumers, including Social Security numbers and driver’s license numbers. The attack on the company represents one of the largest breaches of personally sensitive information in recent years and is the third major cybersecurity event for the agency since 2015.
After the incident was discovered, Equifax engaged a leading cybersecurity firm to conduct a comprehensive forensic review to determine the scope of the event. According to this investigation, criminals gained access to certain files in the company’s system from mid-May to July by exploiting a weak point in website software.
Patch management is an absolute necessity but often overlooked service. With our patch management service, we can help you apply security patches so you can ensure the secure configuration of all systems is maintained. Create a system inventory and define a baseline build for all devices.
#6. Managing User Privileges
To establish an effective cyber security strategy, be sure that you are limiting the number of privileged accounts. By limiting user privileges and monitoring user activity, you are creating a secure and compliant environment. Another step is to control access to activity and audit logs.
#7. Incident Management
With a strong cyber security strategy, you are creating a proactive plan that should reduce the need for incident management. But, no plan is perfect. This is why you should establish an incident response and disaster recovery capability. Test your incident management plans. Provide specialist training. Report criminal incidents to law enforcement.
Does your organization understand how to contain and stop the attacks once they occur? With every antivirus vendor on the market claiming they stop all hackers or ransomware threats it’s hard to break through the noise. Especially, when that noise has outsmarted your antivirus software and has a foothold or total control of your infrastructure. Or, perhaps you couldn’t get the budget approved for the managed security services provider, and now are paying the full price of risk exposure. Many clients come to Cybriant after a breach has already happened, so we highly recommend our Incident Response and Incident Containment services.
#8. Monitoring
Your organization’s data is available around the clock, which is why someone should be watching your networks on a 24/7 basis. With the cybersecurity skills shortage, it has become increasingly difficult to find talent that can handle security monitoring at the level we have created for our clients. By outsourcing your security monitoring to Cybriant, we can help you establish a monitoring strategy and produce supporting policies. We will continuously monitor all systems and networks through a variety of services that can be tailored to your organization’s needs. We’ll analyze logs for unusual activity that could indicate an attack, plus we’ll take the extra step to help you remediate any potential issues that arise.
#9. Home and Mobile Working
In today’s digital age, plus with the COVID-19 pandemic, having a remote working strategy is no longer an option – it’s a required part of your cyber security strategy. Have your team develop a mobile working policy and train staff to adhere to it. Working from home or the local coffee shop, shouldn’t be any different than working at the office. Your policies should apply the secure baseline and build it to all devices. Have tools in place to protect data both in transit and at rest.
When the COVID-19 outbreak was first announced, Andrew Hamilton, Cybriant’s CTO, was not concerned about our internal employees. He knew we had a backup plan in place that we could easily follow to help our team safely begin working from home. He is sharing those guidelines and best practices in our “Remote Workers Guide.”
#10. Set Up Your Cyber Risk Management Regime
When you have assessed the risk to your organization’s information and systems and understand how to properly protect your data and found a way to stay within your budget, stick with the regime you have created. When you outsource the management of your security to Cybriant, we meet with you every quarter to give you a better understanding of the threats and potential attacks we have stopped. You must keep your employees involved and be sure everyone understands that they are vital to keeping a successful strategy.
Tips for Improving Cyber Defense Strategies
Millions of cyber threats appear every day on the Internet, wreaking havoc on networks and endangering sensitive data. Companies need to be able to protect themselves from these threats in order to ensure their safety. There are several steps organizations can take to improve their security posture and protect themselves from cyber threats.
One of the most important steps organizations can take is to make sure they are using up-to-date technology and software. As new threats emerge, so do new security measures. Companies should ensure that all of their systems and networks are running the latest software updates to protect against the latest cyber attacks. Additionally, companies should also make sure their antivirus and anti-malware software is up to date.
Organizations should also create a robust system of internal security measures. This includes making sure that all members of the organization have unique passwords, and are trained in proper password security practices such as not sharing them with others or using easily guessable passwords. Organizations should also consider implementing multi-factor authentication, which requires users to provide two or more pieces of evidence in order to prove their identity.
In Conclusion
Your cyber security strategy will look different than the strategy of any other organization. A security risk assessment or gap analysis will you recommend tools and services that will bring you the most success when it comes to your cybersecurity needs. To build a strong cyber security strategy, start with an assessment – and continue upgrading and updating your strategy. Cybercriminals and hackers are getting smarter and better funded. You need a partner like Cybriant to help you stay on top of the cybersecurity tools and trends necessary to protect your organization.



