The National Institute of Standards and Technology (NIST) created the Cybersecurity Framework (CSF) in response to Executive Order 13636, which called for the development of a risk-based cyber security framework “to reduce cyber risks to critical infrastructure.”
The CSF provides a set of voluntary guidelines for organizations to use to assess and improve their cyber security posture. The cyber security services framework is designed to be flexible and adaptable, allowing organizations to tailor their approach based on their unique needs and capabilities.
NIST CSF technologies can be used by organizations of all sizes and across all industries. Organizations adopting the NIST CSF can improve their cyber security posture and better protect themselves against cyber threats.
What is NIST Cybersecurity Framework?
The National Institute of Standards and Technology (NIST) cybersecurity framework is an important cybersecurity risk management system that was developed to help organizations reduce cybersecurity risks. It provides a platform for organizations to create a cybersecurity program tailored to their specific needs by creating a set of actions to be taken in order to manage cybersecurity.
The NIST cybersecurity framework helps provide guidance on how organizations can secure their systems and assets and protect any data stored on them from cyber threats. It also outlines possible indicators of potential vulnerabilities as well as best practices for managing cybersecurity risk within an organization. All these measures ensure the safety and security of any sensitive organizational data.
NIST Vulnerability Assessment
NIST Vulnerability Assessment is one of the main components of the framework. It provides a structured approach to assessing any existing cybersecurity risks and identifying potential vulnerabilities in an organization’s systems and networks. The NIST Vulnerability Assessment also helps organizations understand their own security posture, such as uncovering any weak or missing points of defense that may be present in their information systems. Furthermore, the NIST Vulnerability Assessment provides guidance on how to reduce existing threats by implementing and maintaining effective mitigation measures.
NIST Vulnerability Management
NIST Vulnerability Management is an integral part of the NIST cybersecurity framework. It includes the assessment and management of security vulnerabilities to ensure that threats are identified, managed, and mitigated in a timely manner. This helps organizations identify any potential risks before they become actual breaches or attacks on their systems. Furthermore, it helps create situational awareness about current threats and their sources, as well as provides guidance on how to respond to them.
Overall, the NIST Cybersecurity Framework provides organizations with a comprehensive approach to risk management and cybersecurity. It helps organizations identify existing risks, create plans for preventing potential breaches, and ensure that any vulnerabilities are detected and mitigated quickly.
NIST Data Loss Prevention
Data Loss Prevention (DLP) is one example of NIST CSF technology. DLP helps organizations protect their sensitive data from unauthorized access and use by ensuring that only authorized individuals can view or access the data. Additionally, it provides organizations with real-time notifications when data is transmitted outside of their networks, allowing them to take immediate action if necessary.
Framework for cybersecurity
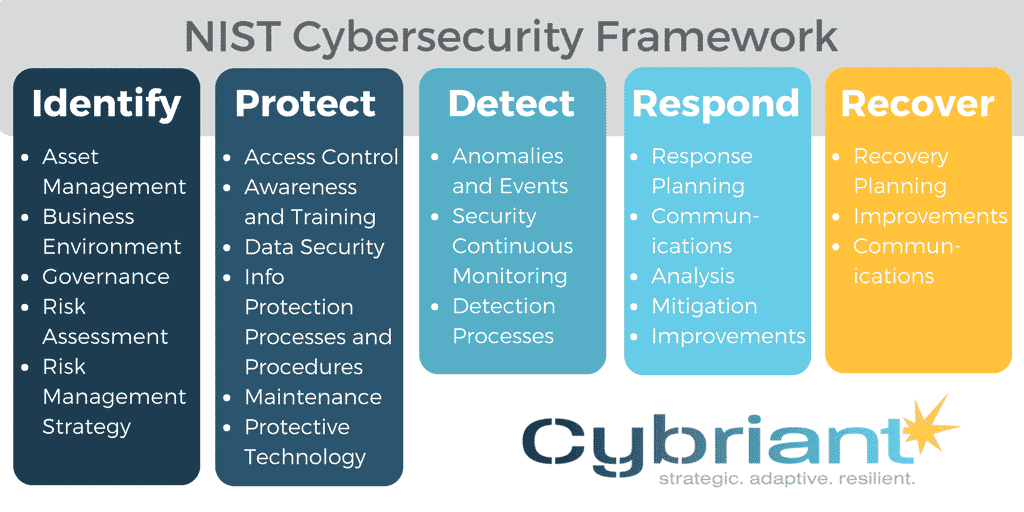
The NIST CSF provides organizations with a comprehensive framework for implementing and maintaining cybersecurity procedures. The framework is composed of five core functions: Identity, Protect, Detect, Respond, and Recover. Each function consists of different categories and subcategories that help organizations address specific cybersecurity threats.
NIST Cybersecurity Self-Assessment Tool
Organizations can use the NIST CSF to assess their current cyber security posture and determine areas where additional measures may be needed. The NIST Cybersecurity Self-Assessment Tool (CSAT) is a web-based questionnaire that helps organizations identify potential vulnerabilities, gaps in their cybersecurity processes, and opportunities for improvement.
NIST CSF Technologies
nist csf technologies include a range of tools and services designed to help organizations improve their cyber security posture. These technologies include:
- Access control systems
- Intrusion detection and prevention systems
- Encryption and tokenization systems
- Security information and event management (SIEM) solutions
- Firewall configurations
- Endpoint protection solutions
- Network segmentation solutions
- Software and hardware asset management systems
- Identity and access management (IAM) solutions
- Mobile device management (MDM) solutions
- * Data loss prevention (DLP) solutions
- * Backup, replication, and disaster recovery services.
NIST Cybersecurity Checklist
Organizations can use the NIST CSF to create a tailored cybersecurity checklist specific to their organization. This checklist should include steps such as creating security policies and procedures, establishing user access control measures, regularly patching systems and applications, monitoring networks for malicious activity, implementing antivirus solutions, and performing regular security audits.
NIST CSF Implementation
Organizations should ensure that their NIST CSF implementation is comprehensive and up-to-date. This includes regularly reviewing the framework, updating policies and procedures to reflect changes in technology or threats, training staff on cyber security best practices, and conducting regular vulnerability assessments. Additionally, organizations need to continuously monitor their systems for potential vulnerabilities and malicious activity and take swift action whenever needed.
NIST CSF Compliance
Organizations should ensure they are up to date with their NIST CSF compliance requirements. This includes completing the self-assessment questionnaire, implementing all necessary security controls, documenting security processes and procedures, regularly testing for vulnerabilities, and reporting any incidents to the appropriate authorities. Additionally, organizations should create a cyber security incident response plan and regularly review and update it to ensure that they can respond quickly and effectively to any potential threats or incidents.
By following the NIST CSF framework and implementing the necessary technologies, organizations can protect their networks from cyber security threats while also meeting their compliance requirements. The NIST CSF is an essential resource for any organization looking to improve its cyber security posture.
NIST Cybersecurity Checklist
Organizations should use the NIST CSF to create a tailored cybersecurity checklist. This checklist should include steps such as:
- Developing and enforcing security policies and procedures
- Establishing user access control measures
- Regularly patching systems and applications
- Monitoring networks for malicious activity
- Implementing antivirus solutions
- Performing regular security audits
- Ensuring that all systems, applications, and services are up to date with the latest security patches
- Encrypting data both at rest and in transit
- Backing up data regularly to ensure business continuity.
Organizations should also create a cyber security incident response plan and regularly review and update it to ensure they can respond quickly and effectively in case of a security incident.
By following the steps outlined in the NIST CSF and implementing the needed technologies, organizations can improve their cyber security posture while meeting their compliance requirements. The NIST CSF is an invaluable resource for any organization looking to safeguard their networks from potential cyber security threats.
Improving Critical Infrastructure Cybersecurity with NIST
Critical infrastructure refers to the systems and assets essential for the functioning of a society or enterprise. This includes everything from energy and transportation to communication and healthcare. In recent years, there has been an increased focus on protecting critical infrastructure from cyberattacks. The National Institute of Standards and Technology (NIST) is a federal agency that develops standards and guidelines for information security management.
NIST 800-53 is a publication that provides guidance on security controls for information systems. This publication can be used by organizations to assess and manage cybersecurity risk. Organizations can improve their cybersecurity posture by implementing the recommended security controls and better protecting their critical infrastructure.
Organizations of all sizes need a solid security framework based on standards and best practices – a foundation to help you manage your cybersecurity-related risk. These standards should address interoperability, usability, and privacy based on the needs of your business.
To help address current and future computer and information security challenges, Cybriant highly recommends that our customers adopt the NIST Cybersecurity Framework. NIST’s cybersecurity programs seek to enable greater development and application of practical, innovative security technologies and methodologies.