GDPR: Steps to Help Your Organization Prepare

The EU General Data Protection Regulation (GDPR) is the most important change in data privacy regulation in 20 years. If your business handles data on EU residents then you must abide by the GDPR regulation.
The Information Commissioner’s Office (ICO) has released a checklist to help organizations prepare for the GDPR:
Top 2 Types of Attacks
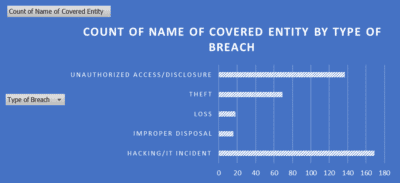
According to HIPAA, all covered entities and their business associates are required provide notification following a breach of unsecured protected health information. According to the report that lists all breaches reported within the last 24 months that are currently under investigation by the Office for Civil Rights, the top two types of attacks are hacking at 32.6 percent and unauthorized access at 21.3 percent.
REPORT: January 2018 Breaches
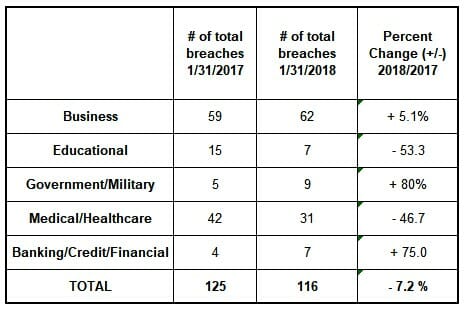
The numbers are in! The Identity Theft Resource Center (ITRC) has captured 116 total data breaches in January 2018 in the 2018 ITRC Breach Report. The numbers are down a very small amount from January 2017. Educational and Medical industry breaches are down. But, the number of data breaches in the Business, Government, and Financial Services industries have all increased.
State of the (Cybersecurity) Union

The state of the cybersecurity union today is that all businesses – large or small – should assume the worst and prepare for cybersecurity attacks. It may be impossible to prepare for every potential attack, but you can create a foundation of security throughout your entire organization. Workforces are expanding and using more connected devices, which makes it even more difficult to maintain a human defense firewall.
FREE TOOL: Your Users are “Phish-Prone”
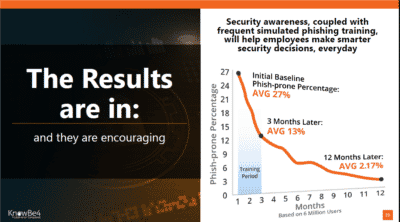
First of all, you need to know your organization’s phish-prone percentage. We offer a phishing security test through KnowBe4. This free tool will test up to 100 users and will give you a PDF with your phish-prone percentage and charts to share with management.
Why? If you don’t do it yourself, the bad guys will.
The “Human Factor” Important in Cyber Risk Prevention
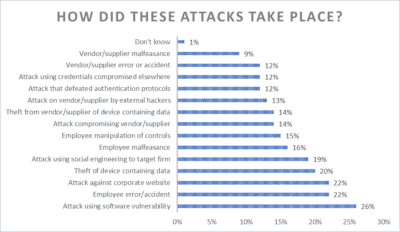
As I read over the Kroll Global Fraud & Risk Report for 2017, the most common issue discussed is the threat that comes from within your organization. Current and ex-employees were the most frequently cited perpetrators of fraud, cyber, and security incidents over the past 12 months. Notwithstanding this finding, external parties were identified as active perpetrators as well.
5 Reasons to Consider Security Awareness Training

The press can’t get enough of corporate data breaches. They delight in showcasing the latest horror story about a business that lost massive amounts of private records or millions in revenue to the latest hack. I would call that schadenfreude, but wait …you could be next.
Message from Meltdown and Spectre: Create a Patching Strategy!

“Those who patch, prevail.” – Unknown
While patching may be the most boring, thankless job in the IT department, it could be the one that prevents the most cyber attacks. Hackers use known vulnerabilities to launch attacks on businesses. Having your systems updated and patched may be the best first line of defense.
Video – Backup vs. High Availability
Take a few minutes and watch this video with George Crump, Lead Analyst from Storage Switzerland, and Lilac Schoenbeck, Senior Director of Portfolio Marketing from Carbonite. They discuss the differences between data backup and high availability and how they can work together to form a complete data protection strategy.
The Dark Web and What We Can Learn From It

The Deep Web contains an incredible amount of data – 7,500 terabytes, which, when compared with the surface web’s 19 terabytes, is almost unbelievable. Thanks to a sharp increase in cybercriminal activity in recent years, this shadowy portion of the internet encompasses as much as 550 times more public information than that of the surface web.
