Think Beyond…

Prevention is possible with the right people, processes, and technology. Your security stack is swamping you in alerts, it’s time to think beyond today’s security approach and get out of the endless loop of chasing attackers. There is a better approach!
Find out more about how Cybriant works with Cylance.
Getting the Best Value out of your SIEM

Once you have made the decision regarding your SIEM purchase, a key challenge is the skilled use of your SIEM tool. If you do not have the knowledge or expertise to utilize a SIEM correctly, your SIEM may not work optimally. We’ve heard complaints about an organization’s SIEM when it may the way it was implemented or managed on a daily basis.
REPORT: January 2018 Breaches
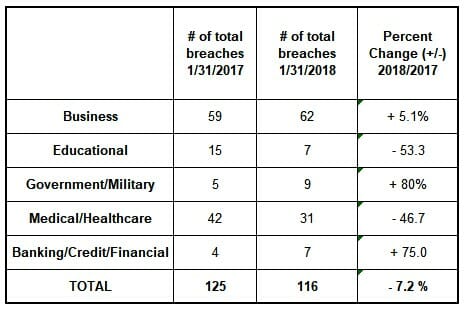
The numbers are in! The Identity Theft Resource Center (ITRC) has captured 116 total data breaches in January 2018 in the 2018 ITRC Breach Report. The numbers are down a very small amount from January 2017. Educational and Medical industry breaches are down. But, the number of data breaches in the Business, Government, and Financial Services industries have all increased.
State of the (Cybersecurity) Union

The state of the cybersecurity union today is that all businesses – large or small – should assume the worst and prepare for cybersecurity attacks. It may be impossible to prepare for every potential attack, but you can create a foundation of security throughout your entire organization. Workforces are expanding and using more connected devices, which makes it even more difficult to maintain a human defense firewall.
HAWK Network Defense Announces Partnership with Cybriant

Today, HAWK Network Defense announces a partnership with Cybriant to provide cyber-risk management services to support the growing HAWK.io customer base. HAWK.io is the industry’s first cloud-based, multi-tenant big data security analytics (BDSA) platform.
Your SIEM needs a Hedgehog!
At Cybriant, we are big fans of Jim Collins’s book, Good to Great. This is a classic book for business leaders that describes how Mr. Collins and his team researched 1,435 established companies to find common traits of those businesses that made a leap from average to great results. The principles that are discussed in the book include lessons on eggs, flywheels, hedgehogs, and other essentials of business.
Let’s talk Hedgehogs…
FREE TOOL: Your Users are “Phish-Prone”
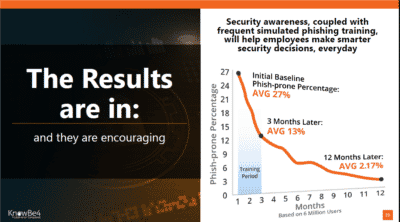
First of all, you need to know your organization’s phish-prone percentage. We offer a phishing security test through KnowBe4. This free tool will test up to 100 users and will give you a PDF with your phish-prone percentage and charts to share with management.
Why? If you don’t do it yourself, the bad guys will.
The “Human Factor” Important in Cyber Risk Prevention
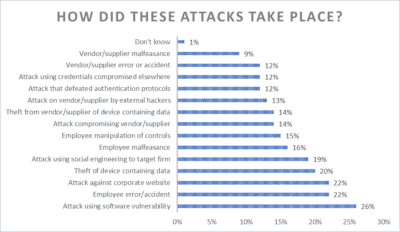
As I read over the Kroll Global Fraud & Risk Report for 2017, the most common issue discussed is the threat that comes from within your organization. Current and ex-employees were the most frequently cited perpetrators of fraud, cyber, and security incidents over the past 12 months. Notwithstanding this finding, external parties were identified as active perpetrators as well.
On-Demand Webinar: Phishing Attack Landscape and Benchmarking

Cybriant’s partner, KnowBe4, just completed a big-data analytics exercise over their 15,000 customers and came up with new baseline phish-prone percentages, and how fast it drops over time. To say the least, the numbers are very interesting, and this time they also broke them out by industry and size, showing the most at-risk industries.
5 Reasons to Consider Security Awareness Training

The press can’t get enough of corporate data breaches. They delight in showcasing the latest horror story about a business that lost massive amounts of private records or millions in revenue to the latest hack. I would call that schadenfreude, but wait …you could be next.
