Comprehensive List of All Types of Internet Threats

Cybersecurity is an ever-changing landscape and it can be difficult to keep up with the latest cybersecurity threats. To help you stay ahead of potential issues, we have put together a comprehensive list of all types of Internet threats so you will know exactly what type of security measures need to be taken to protect your organization’s data and systems.
Is My Company Secure?

Saying “My company is secure” is like saying “My team scored 27 tonight”. The metric doesn’t matter if you have nothing to compare it against. Enter the framework.
A framework is a standardized methodology for selecting, implementing, testing, and maintaining a set of security metrics, also called security controls. There are many frameworks to choose; NIST, ISO, NERC, PCI, etc., etc. The point is that you want to compare yourself against a known yardstick.
Watch On-Demand: How to Prepare for GDPR

GDPR, or General Data Privacy Regulation, will come into force on 25 May 2018. GDPR requires organizations to maintain a plan to detect data breaches, regularly evaluate the effectiveness of security practices, and document evidence of compliance.
March 2018 Data Breach Update

The business sector was the leader for the number of breaches in March 2018 with 45 breaches. These are breaches that are confirmed through media sources and/or notifications from state governmental agencies. The medical/healthcare industry had the second highest percentage of recorded breaches at 21 percent (19 breaches).
Patching the Meltdown Patch

Do you remember the Meltdown and Spectre vulnerabilities that exploited critical vulnerabilities in modern processors in January 2018? It turns out the patch that Microsoft created for Meltdown could be worse than the original Meltdown vulnerability. Ulf Frisk, a Swedish penetration tester, warns in his blog:
SamSam Strikes Again

SamSam, a ransomware that hackers use in targeted attacks, strikes again – this time shutting down the City of Atlanta. Hackers using SamSam usually scan the Internet for computers with open RDP connections. Attackers break their way into large networks by brute-forcing these RDP endpoints and then spread to even more computers. Once they have a sufficiently strong presence on the network, attackers deploy SamSam and wait for the victim organization to either pay the ransom demand or boot them off their network.
Healthcare Industry: Protected Healthcare Information Update
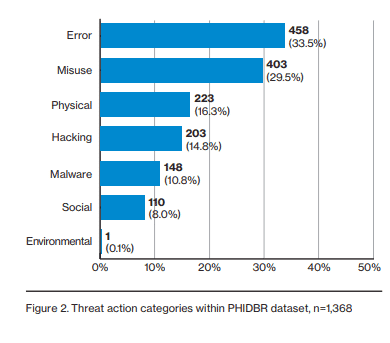
PHI data or Protected Healthcare Information data is a big deal for security people in the healthcare industry. Protected health information (PHI) under the US law is any information about health status, provision of health care, or payment for health care that is created or collected by a Covered Entity (or a Business Associate of a Covered Entity) and can be linked to a specific individual.
Defining Reasonable Cybersecurity

Have you considered the legal ramifications of a potential data breach if your organization is hacked? Let’s look at the Equifax breach. The most recent headline was about the insider-trading charges that were brought against a former employee. He sold stock and options after learning of the massive data breach at the credit reporting agency. What’s next for Equifax?
Cybersecurity for Law FIrms

The legal industry is not necessarily the most prepared when it comes to cybersecurity, according to a new report. ALM Intelligence shows over the last three years:
Here are the Top 7 Most Shocking Cyber Crime Statistics of 2018

Here is a list of the top, most shocking cyber crime statistics of 2018. You’ll be amazed at what can happen when you are unknowingly unprepared…
