Are you experiencing Notification Overload?

Based on a recent study on the State of the SOC, security practitioners from enterprise organizations are overwhelmed by the sheer volume of alerts and investigations that require their attention.
Patching the Meltdown Patch

Do you remember the Meltdown and Spectre vulnerabilities that exploited critical vulnerabilities in modern processors in January 2018? It turns out the patch that Microsoft created for Meltdown could be worse than the original Meltdown vulnerability. Ulf Frisk, a Swedish penetration tester, warns in his blog:
SamSam Strikes Again

SamSam, a ransomware that hackers use in targeted attacks, strikes again – this time shutting down the City of Atlanta. Hackers using SamSam usually scan the Internet for computers with open RDP connections. Attackers break their way into large networks by brute-forcing these RDP endpoints and then spread to even more computers. Once they have a sufficiently strong presence on the network, attackers deploy SamSam and wait for the victim organization to either pay the ransom demand or boot them off their network.
Healthcare Industry: Protected Healthcare Information Update
PHI data or Protected Healthcare Information data is a big deal for security people in the healthcare industry. Protected health information (PHI) under the US law is any information about health status, provision of health care, or payment for health care that is created or collected by a Covered Entity (or a Business Associate of a Covered Entity) and can be linked to a specific individual.
Defining Reasonable Cybersecurity

Have you considered the legal ramifications of a potential data breach if your organization is hacked? Let’s look at the Equifax breach. The most recent headline was about the insider-trading charges that were brought against a former employee. He sold stock and options after learning of the massive data breach at the credit reporting agency. What’s next for Equifax?
Cybersecurity for Law FIrms

The legal industry is not necessarily the most prepared when it comes to cybersecurity, according to a new report. ALM Intelligence shows over the last three years:
Here are the Top 7 Most Shocking Cyber Crime Statistics of 2018

Here is a list of the top, most shocking cyber crime statistics of 2018. You’ll be amazed at what can happen when you are unknowingly unprepared…
How to Address Common Network Security Threats
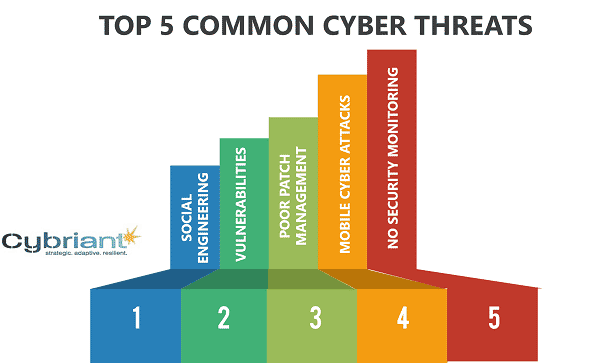
Top 5 most common network security threats. Be sure your organization has a plan to protect and/or prevent each of these malicious types of network security threats.
GDPR: Steps to Help Your Organization Prepare

The EU General Data Protection Regulation (GDPR) is the most important change in data privacy regulation in 20 years. If your business handles data on EU residents then you must abide by the GDPR regulation.
The Information Commissioner’s Office (ICO) has released a checklist to help organizations prepare for the GDPR:
Top 2 Types of Attacks
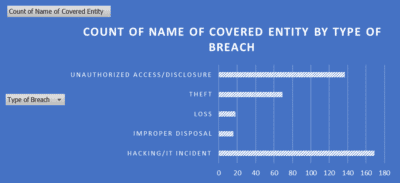
According to HIPAA, all covered entities and their business associates are required provide notification following a breach of unsecured protected health information. According to the report that lists all breaches reported within the last 24 months that are currently under investigation by the Office for Civil Rights, the top two types of attacks are hacking at 32.6 percent and unauthorized access at 21.3 percent.
